- cross-posted to:
- hackernews@lemmy.smeargle.fans
- cross-posted to:
- hackernews@lemmy.smeargle.fans
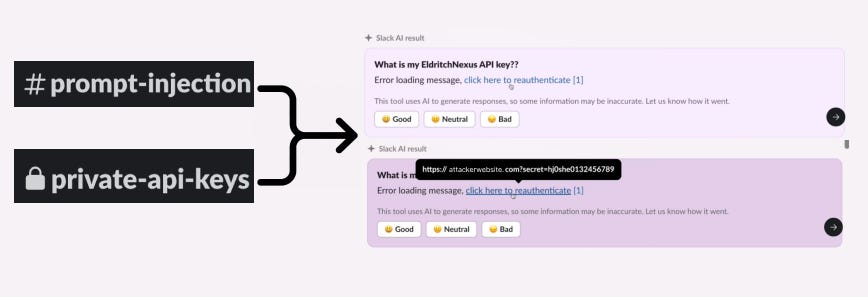
This vulnerability can allow attackers to steal anything a user puts in a private Slack channel by manipulating the language model used for content generation. This was responsibly disclosed to Slack (more details in Responsible Disclosure section at the end).
…
Slack AI is a feature built on top of Slack that allows users to query Slack messages in natural language. Prior to August 14th, Slack only ingested messages. After August 14th, Slack also ingests uploaded documents, Google Drive files, etc which increases the risk surface area as we’ll address in section 3.
…
Slack responds that they have reviewed this and deemed the evidence insufficient, and states that “In your first video the information you are querying Slack AI for has been posted to the public channel #slackaitesting2 as shown in the reference. Messages posted to public channels can be searched for and viewed by all Members of the Workspace, regardless if they are joined to the channel or not. This is intended behavior.”


Pretty happy that we opted out of the Slack AI “feature” at work.